Azure AD Join with automatic MDM enrollment – Deploy and upgrade operating systems
Azure AD Join with automatic MDM enrollment
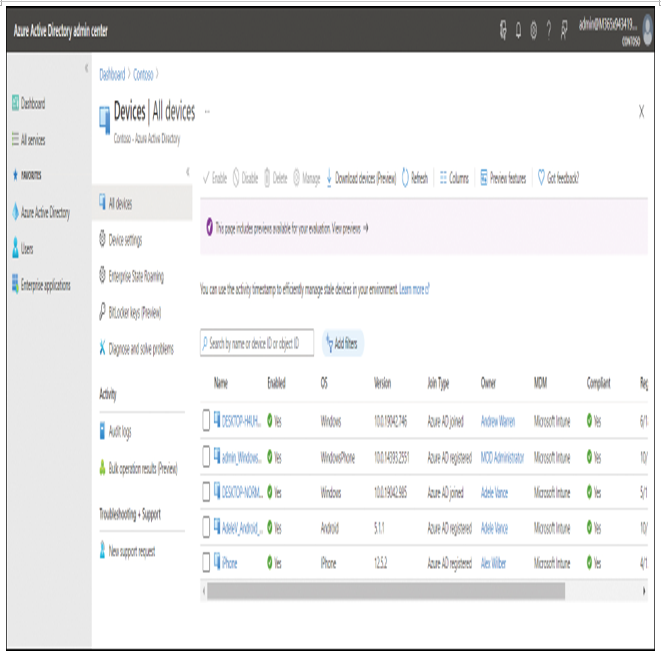
You can dynamically provision Windows 10 devices using Azure AD and a Mobile Device Management (MDM) solution, such as Microsoft Intune. Once a device is enrolled into management, Microsoft Intune can deploy compliance and corporate security policies to the device in a similar way (but not the same) as Group Policy objects are used within a domain-based environment to configure computers.
MDM can be used to add or remove apps, restrict device features, and more. Through the application of MDM policies, Azure AD can block or allow access to corporate resources or applications based on the status of the device compliance.
To benefit from the cloud-based dynamic provisioning, you need the following requirements:
- Windows 10 Pro or Windows 10 Enterprise
- Azure AD for identity management
- A mobile device management solution, such as Microsoft Intune
Perform Azure AD join
In a traditional domain-based environment, the protection of user identities is a major security concern. With a username and password, a malicious hacker can cause havoc on any system. For a cloud-enabled workplace, the device is also a key component of your infrastructure. In a similar way to the user, the device is another identity that you need to protect. Azure AD allows you to join Windows 10–based devices to the cloud-based directory, and you can provide management tools to keep the device healthy and safeguarded.
For some businesses, the traditional on-premises model serves them, and they may not want to (or need to) change. Azure AD works very well in the following scenarios:
Cloud-based services and resources When most of the applications and resources that the organization uses are in the cloud, such as Microsoft 365 apps (Office 365 ProPlus) or Dynamics 365, joining client devices to Azure AD can increase the usability and ease of access.
Bring Your Own Device (BYOD) Users can join their devices to your business environment. Azure AD can manage and protect resource access for Windows 10 and non-Microsoft devices, such as iPads or Android tablets, that cannot join an AD DS domain. Personal and business data can be kept separate, and business data can be wiped from the device when the device leaves (or is removed from) management.
Mobility of the workforce Many organizations have employees working remotely or from home. In settings where workers infrequently visit a traditional on-premises domain environment, opting for a cloud-based management solution could be beneficial. Azure AD and Intune support the joining and remote management of mobile devices such as laptops, tablets, and smartphones.
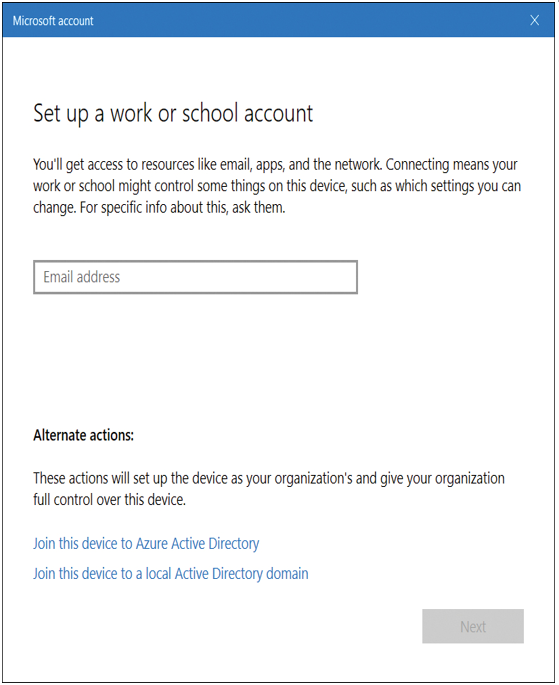
Users can join Windows 10 devices to Azure AD during initial Windows 10 setup, or a device can be joined at a later stage by using the Settings app. Windows 10 devices can connect to Azure AD in several ways, as follows:
- Join a new Windows 10 device to Azure AD
- Join an existing Windows 10 device to Azure AD
- Register a Windows 10 device to Azure AD
Exam Tip
You can only join Windows 10 devices to Azure AD. iOS and Android devices can be registered but not joined.